NOTE: This blog has been merged with WordPress. You will be redirected to this article on the WordPress site in 10 seconds...
If you want to go there now, click here - https://hazmalware.wordpress.com/2017/01/05/hancitor-maldoc-analysis/
I see a lot of malicious documents in my line of work and as with many people who follow threats, I see quite a bit of hancitor. Also known as chanitor and tordal, hancitor is a dropper or downloader malware designed gain a foothold and install 2nd stage malware on systems. It is primarily delivered through phishing emails with document attachments, but has also been installed through exploit kits. After being installed on a victim computer hancitor will download its secondary payloads of pony, a credential stealer, and vawtrak which is a banking trojan with various modules that also has the ability to perform data exfiltration.
Most of the hancitor maldocs that i have analyzed recently have had the malware payload embedded in the document itself which it then extracts and decodes through VBA script. This one, however, took a slightly different approach and used obfuscated VBA to invoke powershell to download and execute the payloads. This approach is not new by any means, but was a slight shift from standard activity that I have observed recently, and thus I felt warranted note. Let's begin.
Following typical behavior, this maldoc had the standard warning for users telling them that it is 'protected' and they must enable editing and content so the malware can be installed.
Those who keep up with hancitor are familiar with the magic identifiers which mark hancitor maldoc embedded payloads, such as NICEWORK and STARFALL. These identifiers follow a fairly standard pattern of 8 alpha characters followed by the hex values 0x08 0x00 shown here:
This document did not contain any of the known magic identifiers. Additionally it did not appear to have a payload embedded in it.
Pulling the metadata from the document we see a few things of note. It shows the create_time and last_save_time as 12/15/2016. Shows the author and last_saved_by as a user 'home'. Additionally it displays the codepage as 1251 ANSI Cyrillic. This should not be surprising as it is a well known fact that hancitor is used pretty heavily by Eastern European based threat actors.
Inspecting the document structure shows that there is a single section that contains VBA macros, listed as ThisDocument, as shown on stream 8 denoted with a 'M'.
Time to extract the VBA and have a look...
This is basically extra code that does not serve any real purpose other than to confuse analysts and try to bypass antivirus checks. This technique is used by almost every malicious document I have come across. There is quite a lot of junk code in this document; in fact we don't see any legit code until we get all the way down to line 490.
Here is another interesting function that appears to be performing a XOR operation. This is yet another trick designed to make analysis more difficult. Lucky for us the XOR value is displayed in plain sight so we can easily reverse this operation if needed.
And finally we see a Shell() function. This is typically where the final actions are carried out, such as downloading payloads, starting processes, etc.
The Shell() function takes arguments as input and executes an external program. Looking at Microsofts documentation for Office VBA says the function takes 2 arguments, pathname & window style.
If we really wanted to we could cheat now and just remove the last variable; change the Shell() function to a MsgBox() so that it displays the values being passed instead of executing them.
But where is the fun in that?
After removing thousands of lines of junk code and fixing some of the formatting this is what we are left with; roughly 33 lines of actual malicious VBA code.
We essentially have 2 declared functions, dateddiffInputboxConst() and sconsts(); and one 'main' function with Document_Open(). If you notice all of the variables and functions are given random nonsense names. This is just another layer of the obfuscation technique used to make analysis harder. These variables and functions get renamed during the obfuscation process used by the threat actors.
For the purposes of this blog post I have renamed all the variables and functions to make understanding the code easier, and our analysis run smoother. This is what it looks like now.
First let's examine the Document_Open() function. As stated earlier, this function will execute when the document is opened. I know... big surprise! This requires the victims Microsoft Office security settings to have macros enabled before that will happen, which is more than likely not the case 99% of the time because they are disabled by default in most all recent versions.
Right away there are 8 variable string declarations with Dim <variable-name> As String. After each variable is declared it is assigned a value of the result of the string passed to the buildString() function. The string is much longer than the value shown here, but it just contains a bunch of 3 digit numbers separated by commas.
Examining that function shows the following:
- It takes a string as an input
- Creates a one-dimensional array using all of the values of tempString split by ',' for example if we use the values of tempString1 shown above, the first element, theArray[0], would be 215; followed by theArray[1] with value 222, then 151, etc.
- Gets the size of the array, or the number of elements in the array
- Creates a For loop to loop through each element of theArray
- Builds a string by concatenating the result of the function getAsciiChar() which is passed the character in the current array element theArray[counter] XOR'd by 185.
- Returns the newly created string
Next is the getAsciiChar(), which takes a number charCode as input and performs the Chr() function to return the corresponding Ascii character. Remember the Chr() function from earlier?
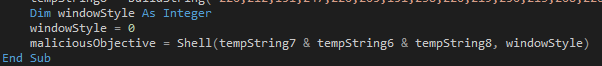
Finally is the last step in this operation, performing the Shell() function to execute the command.
I have labeled this as maliciousObjective - well... because that is what it is. It calls the Shell() function with 3 variables concatenated together as the command and sets the windowStyle to 0. This value means that the window will be started with vbHide set, making it a hidden window.
Now that we have a good understanding of what the code is doing we can try to decode the command that it is executing.
- create a string with a few of the numbers from tempString7 called lame
- create an empty string to hold the results called dumb
- create a for loop, splitting lame by commas, and perform operation on each
- get the character code for the current number XOR'd by 185
- assign that value to dumb and concatenate with the previous value
Performing this operation we see that the result is the string 'cmd /c powershell'. We can now create one string out of the values of tempString7, tempString6, and tempString8 together and run it through the same operation.
This gives us the above which spawns a command prompt and runs powershell to attempt the download of a file called 15.exe from 3 different URLs, saves it as 20800.exe into the users temp directory, and then starts it as a process. This file is the Hancitor dropper malware. After loading it will then attempt to perform C2 and then download pony and vawtrak malware.
One thing I found interesting with this sample is that only 3 of the tempStrings were used when executing maliciousObjective. I wonder what the other strings were for... Let's have a look, shall we?
It took me a few minutes to get the order of the other strings correct because they are not in sequential order. You have to take each remaining tempString, decode it, and then figure out what order they go in. After going through this exercise the resulting string is this javascript:
I am not certain why this other method exists in the document at this time. It could be that the actor was trying out different methods and didn't remove the code; or maybe it is because they wanted an easy way to quickly change tactics. Its difficult to say at this point.
Here is the information on the sample that was analyzed in this post:
Malicious Document
Malicious Document
IOCs related to this threat:
Hancitor payload
MD5 13ec9875aaea2921bbb0e854cdcbf2f6
SHA1 56f321a54a54c9a41d0a30358d287ca98de6360d
SHA256 141cf8161f4850f2f09e6a8651479f125fc27c6d72e2e9f5bf02eabd46156990
Hancitor Payload URLs
hxxp://www.walterkubinski2015[.]com/wp-content/themes/twentyfifteen/15.exe
hxxp://janniekristiansen[.]dk/wp-admin/15.exe
hxxp://vivre-la-fleur.decoration-guadeloupe[.]info/wp-content/plugins/black-studio-tinymce-widget/15.exe
Hancitor C2 URLs
hxxp://seatreledu[.]com/ls5/forum.php
hxxp://rumeinof[.]ru/ls5/forum.php
hxxp://rongaboty[.]ru/ls5/forum.php
Pony Payload
MD5 063adf42a8cad08de610c3f1e6b6819a
SHA1 b1d97712286b0e982f3e04e21bb83cb23922ef4f
SHA256 4fa443b7144bd237e1c1024c7a083ba5771bd0547c8fbd48cf05059171e242d6
Pony Payload URLs
hxxp://granjamaripepa[.]com/wp-content/plugins/wp-migrate-db/pm1.dll
hxxp://clotures-guadeloupe[.]net/wp-admin/pm1.dll
hxxp://termites-guadeloupe[.]com/wp-admin/pm1.dll
hxxp://itrdiagnostics[.]com/wp-admin/includes/pm1.dll
hxxp://ferme-martinique[.]com/wp-admin/includes/pm1.dll
hxxp://mohawkwarriorhockey[.]ca/wp-content/plugins/contact-form-7/pm1.dll
Pony C2 URLs
hxxp://seatreledu[.]com/klu/forum.php
hxxp://rumeinof[.]ru/klu/forum.php
hxxp://rongaboty[.]ru/klu/forum.php
Vawtrak Payload
MD5 0d10ef9d038e62b104498740031758e9
SHA1 66dfe9f620433f53599613f21eb450adb8746df4
SHA256 df18461ff1770826150cbe3abca8f1fef4f89323e0ea91b6337adf135a6173c9
Vawtrak Payload URLs
hxxp://granjamaripepa[.]com/wp-content/plugins/wp-migrate-db/inst2.exe
hxxp://clotures-guadeloupe[.]net/wp-admin/inst2.exe
hxxp://termites-guadeloupe[.]com/wp-admin/inst2.exe
hxxp://itrdiagnostics[.]com/wp-admin/includes/inst2.exe
hxxp://ferme-martinique[.]com/wp-admin/includes/inst2.exe
hxxp://mohawkwarriorhockey[.]ca/wp-content/plugins/contact-form-7/inst2.exe
Vawtrak C2
hxxps://misocgutlah[.]com/index.php
hxxp://31.24.30[.]241/module/
hxxp://qestffovur[.]com:443